DanderSpritz documentation
The goal of this project is to document the different capabilities and functionality of the DanderSpirtz post-exploitation framework by examining the contents of the “resources” folder included in the ShadowBrokers leak and doing live testing of the framework on lab systems.
Note: This is a documentation project that does not contain all of the FuzzBunch code, exploits, binaries, etc. The repository only contains the files found in the Windows/Resources/ directory included in the leak.
If you’re interested in viewing the entire contents of the leak use this repo including the files and data necessary to use the framework, please use this repo:
Disclaimer: This project is intended to be used by information security researchers who are interested in understanding the capabilities of frameworks used by real-life nation state adversaries. I am not responsible if you choose to use my work or this documentation to do something dumb and illegal.
What is DanderSpritz?
DanderSpritz is a modular, stealthy, and fully functional framework for post-exploitation activities on Windows and Linux hosts. The framework contains tools to bypass anti-virus & security tools, disable and delete Windows event logs, establish persistence, perform local and network reconnaissance, move laterally within a network, and exfiltrate data.
DanderSpritz was leaked by The Shadow Brokers on April 14th, 2017 as part of the “Lost in Translation” leak.
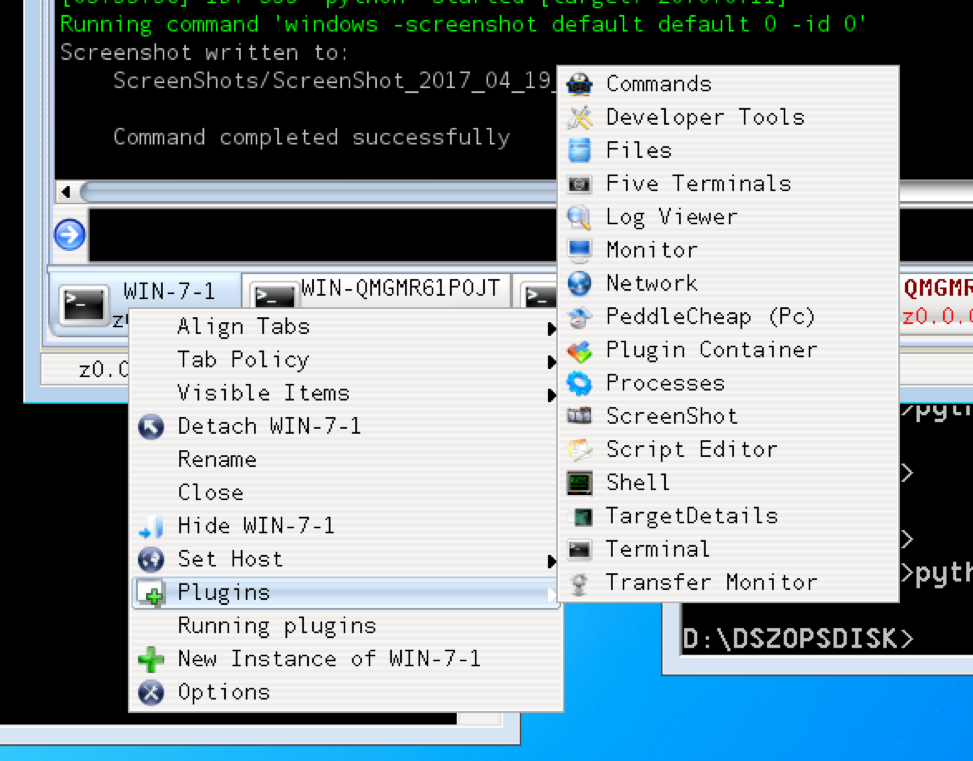
Framework Documentation
- Setting up DanderSpritz
- DanderSpritz Terms & Code Names
- DanderSpritz Operations
- DanderSpritz Plugins (tools) & Commands
- Safety Handlers
- AV & Security Product Bypasses
- Logging Bypasses & Modifications
- Local Reconnaissance
- Network Reconnaissance
- Persistence Methods
- Lateral Movement
- Data Identification and Exfiltration
DanderSpritz lab
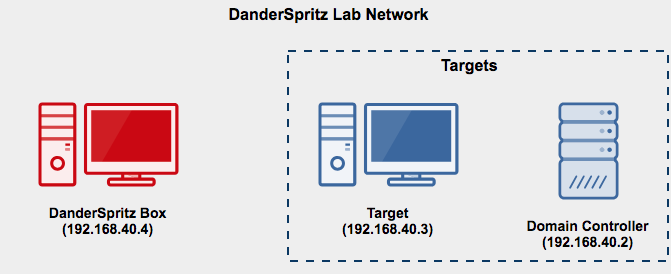
I’ve published DanderSpritz_lab a series of packer and vagrant scripts that build a fully functional DanderSpritz lab in as little as two commands.
If you’re trying to get DanderSpritz up and running in a lab environment quickly - I highly recommend that you use DanderSpritz lab instead of installing and configuring it manually. However, if you would prefer to configure it yourself, please visit the DanderSpritz set up page
Blog Posts
- DanderSpritz Overview Part 1 (Information gathering, AV bypasses, and security auditing bypasses)
- Introducing DanderSpritz_lab (build a fully working lab in as little as 2 commands)
- Blog #3 is coming soon
Presentation
A PDF of my presentation about DanderSpritz at Derbycon 7.0 is available here
A recording of my presentation about DanderSpritz at Derbycon 7.0 is available here